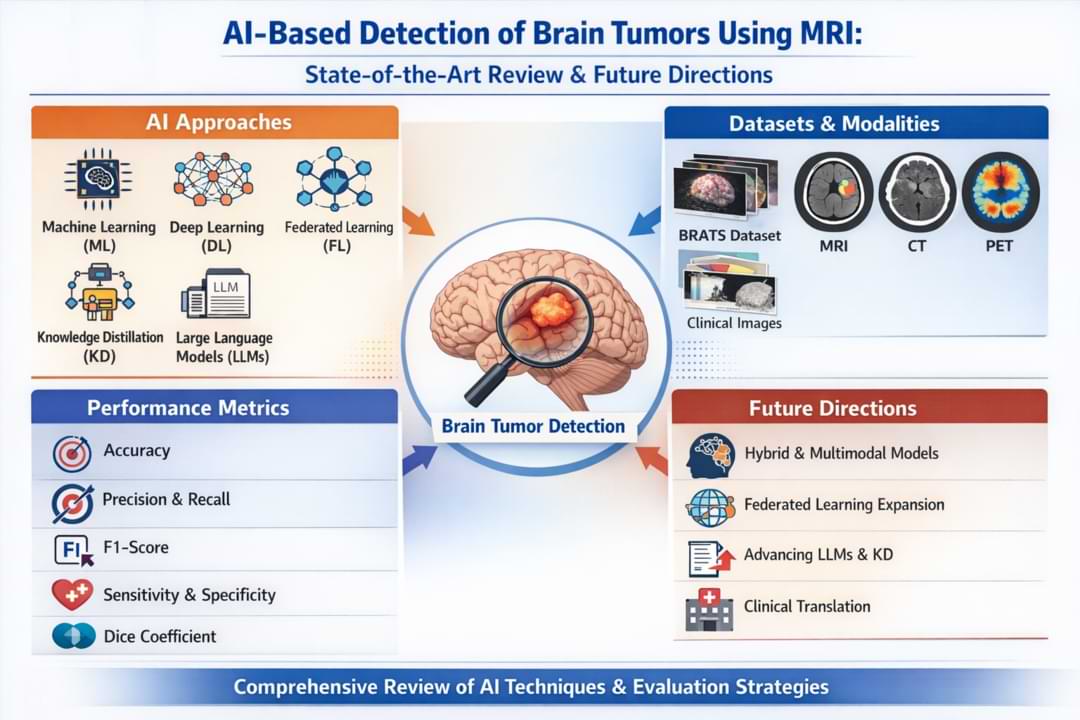
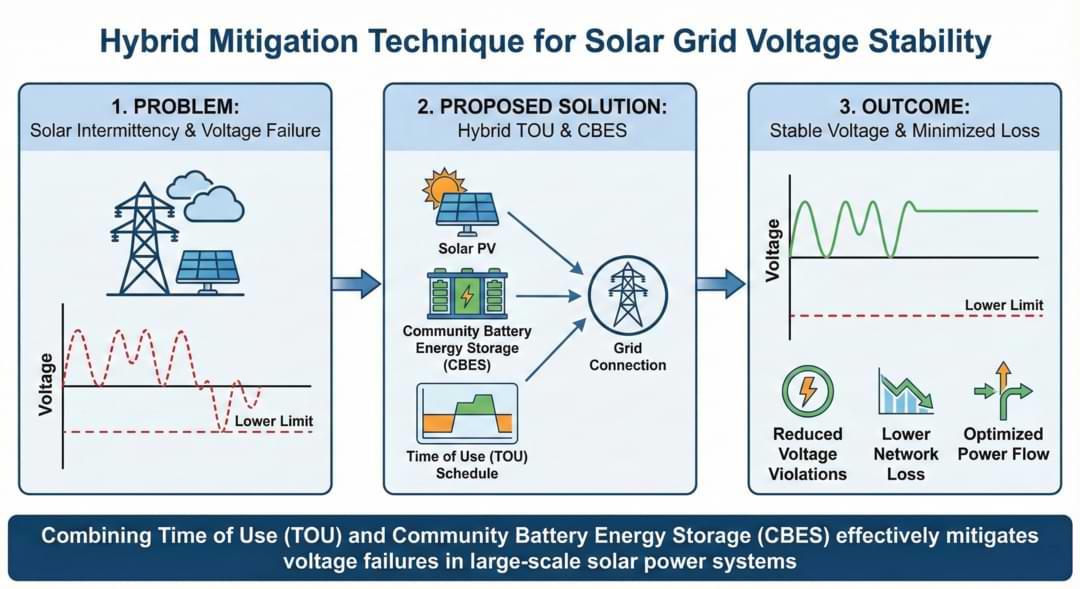
Use of network and cyber security tools to counter the security obstacles
Vol. 6 No. 1 (2022)
Original Research
January 16, 2026
Downloads
Machap, D., & Muaza, A. (2026). Use of network and cyber security tools to counter the security obstacles. Journal of Applied Technology and Innovation, 6(1). https://doi.org/10.65136/jati.v6i1.149
Downloads
Download data is not yet available.
Copyright (c) 2022 Journal of Applied Technology and Innovation

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.