Zero Trust Architecture in Cloud Security: Enhancing Security Posture in the Cloud Era
Downloads
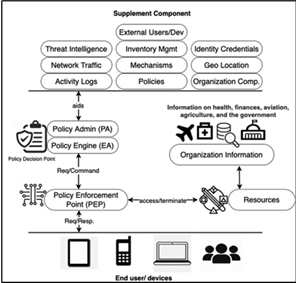
Cloud computing has created new windows for data management while also increasing the weaknesses of old security methods. To address these challenges, Zero Trust Architecture (ZTA) eliminates implicit trust and constantly monitors access requests. This article investigates how to properly integrate ZTA ideas in cloud environments, such as micro-segmentation, multi-factor authentication, and risk-based access controls. It also examines the challenges of adopting ZTA, such as the technology's complexity, budgetary concerns, and the constant evolution of cybersecurity threats. This study demonstrates how ZTA may better protect modern businesses by offering a framework for improving security and offers recommendations for future research paths to further its effectiveness.
Downloads

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.