Focus & Scope Author Guidelines Review Process Manuscript Template Publication Ethics Publication Frequency Open Access Policy Plagiarism Policy Editorial Board Processing Charge
Search
1 - 19 of 19 items
Towards Inclusive Cybersecurity Learning: A Novice-Friendly Capture-the-Flag Onboarding Platform
Abstract : 17
PDF : 13
Enhance Public Cybersecurity Awareness By Understanding Cybersecurity And Cyberthreats
Abstract : 20
PDF : 8
Review on the Enhancement of Cyber Security Policies That Impacts the Employment System
Abstract : 23
PDF : 12
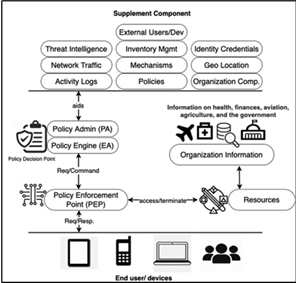
Zero Trust Architecture in Cloud Security: Enhancing Security Posture in the Cloud Era
Abstract : 141
PDF : 14
Simulation, Investigation and Response Towards Log4J Vulnerability (Log4Shell)
Abstract : 21
PDF : 14
Food Donation Application to Improve the Distribution and Verification Process Within Selangor: Feedback
Abstract : 25
PDF : 12
1 - 19 of 19 items